Blog

How to Address Door Access Control System Migrations
Learn how to address door access control system migrations effectively. Discover the benefits of integrating physical and digital security, phased migration strategies, and practical steps to ensure a smooth transition.
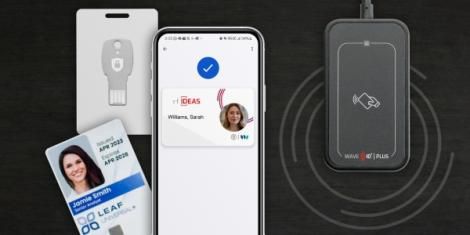
How to Transition from Legacy Technology to Modern Credential Solutions
Transitioning away from legacy technology to modern credential solutions can enhance your organization's security. Explore various modern credential solutions including smart cards, mobile credentials, and FIDO passkeys to mitigate data breaches, unauthorized access, and phishing attacks.

Why Proximity Cards Are Putting Your Organization at Risk of Account Takeovers
The vulnerabilities of outdated credential technologies are putting your org at risk for account takeovers. Learn why it is important to begin transitioning to secure solutions before a breach happens.

Why MFA Is Good for Security
Learn why MFA is good for security and how smart cards, mobile credentials and passkeys help protect against today’s most common cyberthreats.

Breaking Down the Myths of Passwordless Security Deployment
Discover the truth behind passwordless security deployment. Learn how passwordless methods enhance user experience, can integrate with legacy systems, and reduce burdens on IT teams.

Standard MFA and Phishing-Resistant MFA: Explained
AI-driven phishing is evolving fast. Learn how phishing-resistant MFA and FIDO passkeys protect against modern cyber threats.

A Guide to Secure Credentials: The Smart Way to Authenticate Users
Upgrade your access control with secure credentials. Explore smart cards, mobile credentials and FIDO2 passkeys for enhanced security and efficiency.

How rf IDEAS Readers Add Value to Digital Asset Tracking Solution from Pole Star
Learn about innovative digital asset tracking solutions that boost efficiency, reduce theft, and improve patient care. Explore the future of hospital operations with rf IDEAS and Pole Star.

Securing the Future of Retail: Trends in POS Security
How can POS security adapt to face increasing theft incidents and evolving retailer needs? Explore how RFID, biometrics, and AI are revolutionizing cybersecurity in retail and enhancing customer experiences.

What Is a Visitor Management System?
Learn how a visitor management system enhances security, streamlines guest check-ins and improves compliance, creating a seamless experience for all visitors.

Understanding Manufacturing PLC Cybersecurity: Why User Authentication Is Critical
PLC cybersecurity is a critical concern in manufacturing, given how often these devices are targeted. Here’s how you can protect your PLCs from cyber attacks.
The Best Mobile Access Control Solutions in 2025
The case for mobile access control is stronger than ever! Discover how mobile access control solutions offer stronger security and greater flexibility across all end points in your organization. Explore the top mobile credential readers for 2025 and find the perfect fit for your organization’s needs.

The Best Smart Card Readers of 2025
Step into 2025 with secure logical access top of mind. We’ve compiled a list of the top smart card readers of 2025 so you can discover how these cutting-edge devices can protect your assets and streamline your operations.

How to Combat Print Data Security Breaches
Despite rapid digitization, print devices remain essential in many industries, posing significant security risks if left unprotected. Our latest blog explores the dangers of unsecured printing, offers practical steps for implementing secure print solutions, and highlights how WAVE ID® readers can safeguard your sensitive information.

What is SCADA Cybersecurity, and Why is It Important For Manufacturers?
SCADA cybersecurity vulnerabilities can lead to costly downtime for manufacturers. Learn how to modernize your systems to fill security gaps.

What Is a Smart Card Reader? A High-Level Explanation
Paired with contactless smart cards, smart card readers offer a secure and convenient logical access solution for organizations of all sizes.

Built Ready for Manufacturing: How to Improve Security, Accountability and Safety with Embedded OEM Readers
Learn how embedded OEM readers add value to OEMs’ product offerings with built-in identity access capabilities designed for interoperable, future-proof security.

Built Ready for Healthcare: 3 Ways Embedded OEM Readers Immediately Improve Your Medical Product Portfolio
Build authentication capabilities into your medical device portfolio with embedded OEM readers compatible with the leading secure credentials.

Key Takeaways from Authenticate 2024
Explore our key takeaways from FIDO Alliance’s Authenticate 2024 Conference: the benefits, use cases, and differentiators of synced and device-bound passkeys.

rf IDEAS & AuthX: Enhancing Law Enforcement Security with Passwordless Authentication Solutions
rf IDEAS and AuthX are revolutionizing law enforcement security with passwordless authentication solutions, ensuring quick, reliable access when it matters most. With the CJIS compliance deadline approaching, now is the time to enhance your security game. Discover how our integrated solutions provide stronger, simpler security, enhanced efficiency, and easy integration for law enforcement agencies.

Mobile Authentication Systems: Use Cases and Benefits
Traditional authentication methods are no longer sufficient to safeguard organizations against modern cyber threats. Discover how authentication with mobile credentials can enhance your security, improve user experience and streamline access management.

Authentication Methods 101: Credentials, Types and Best Practices Explained
Passwords alone aren’t enough to secure user data. Learn why proper authentication is essential in today’s digital environment and which type of authentication is right for your organization.

How Mobile Authentication Saves Time for Employees
Time is valuable in an enterprise and employees want to seamlessly move throughout their day without friction. With mobile authentication, they can do just that. Walk through an employee’s day from start to finish and discover how mobile credentials can transform user experience for the better.

How Shifting from Prox to Mobile Access Improves Cybersecurity and Reduces Risk
Why should you shift from proximity cards to mobile access? Other than enhancing cybersecurity and reducing risks within the enterprise, mobile authentication can bridge the physical and digital ecosystems that employees navigate daily. Discover how rf IDEAS can help bring mobility to life.
Removing Mobile Integration Complexities to Facilitate Stronger Security
Migrating to mobile made simple. Learn strategies to overcome integration challenges, protect your network and improve user experience with mobile credentials.
How Digital Wallets Provide a Better Experience
If you have used a digital wallet for payment, then you know how simple that process is. Now is the time to explore the benefits of implementing digital wallets for your organization. From enhanced security and streamlined access to versatility and ease of use, digital wallets can provide a better experience for employees and IT professionals.

Thoughts on Frontline Worker Authentication
Frontline workers are the backbone of many industries, yet their authentication needs can be difficult to address effectively. Learn about the aspects of frontline worker environments that can make their authentication challenging and explore what passkeys can offer in terms of a solution.

The Focus of Digital Identity Solutions on Cybersecurity Design
Ready to unlock the future of digital security? Dive into this blog and discover how these cryptographic keys are reshaping the way we safeguard our digital identities.

What Is a Smart Campus? The Next Generation of Campus Connectivity
Today’s students seek a connected educational experience that mirrors their digitally integrated lives. Smart campuses deliver just that. By harnessing advanced technologies, educational institutions can better protect their campuses, elevate their appeal and optimize the student experience.

Logical Access Control vs. Physical Access Control: What’s the Difference?
As cybersecurity threats evolve, understanding the differences between logical access control vs. physical access control becomes paramount. Organizations can take advantage of the convergence of the two access control types to enhance their overall security.

Passwordless Authentication Methods Explained
To protect against the rising tide of cyberthreats and streamline workflows, organizations need to make the transition to passwordless authentication methods, which offer a more secure and user-friendly alternative to traditional passwords.

Access Control with Digital Wallets: Benefits and Uses
People rely on digital wallets for daily tasks like making contactless payments and storing event tickets — and more recently, for many work-related functions. As more organizations leverage digital wallets for logical access control, the use of mobile credentials streamlines and secures access to data and systems.

The State of Passkeys in 2024
While there is currently a high barrier to the adoption of passkeys, they are increasingly considered the next step on the journey towards a passwordless future. Increased education around the deployment of passkeys and the advantages they bring to various enterprise security frameworks can further progress the adoption of the hugely beneficial technology that keeps authentication access consistent and simplified.

What Is Secure Printing? How to Protect Your Sensitive Documents
Network-connected printers and multifunction printers (MFPs) might seem like innocuous pieces of office equipment. But they’re also a security risk organizations often overlook. Learn how secure print solutions can protect organizations from risks like information theft, unauthorized access and compliance violations.

Exploring Single Sign-On (SSO) and How It Works
Juggling passwords and usernames for multiple applications is a headache for employees, and it also leaves your systems vulnerable to breaches and cyberattacks. Learn how SSO can streamline the login process for employees and bolster your organization’s security protections.

A Complete Guide to Mobile Access Control
We trust our smartphones for a growing number of secure activities in our personal lives — so why not at work? Learn why mobile access control is a user-friendly but ultra-secure way to protect your data, devices, systems and equipment.

What Is Logical Access Control? A Comprehensive Guide
The convergence of physical and logical access control opens up new possibilities for securing the enterprise. Learn how to build a comprehensive logical access control strategy to safeguard your data, ensure compliance and streamline operations.

Level Up Attendance Tracking Accuracy for Better Manufacturing Workflows
Explore how attendance tracking solutions can streamline workflows from the plant floor to the back office.

Biometric Authentication Solutions Are One of Government Agencies’ Strongest Defenses Against Cyberthreats
Government agencies should consider biometric authentication solutions as a part of their security tech stack. Here’s why.

3 Ways Logical Access Control Helps Health Networks Protect Patient Data
Learn why healthcare data is a prime target for hackers and how logical access control can keep healthcare organizations one step ahead.

How Secure Print Solutions Provide Peace of Mind to Financial Institutions
Financial institutions should make secure print solutions a key element of their tech stack. Read on to find out why.

rf IDEAS + IDAC Podcast
Listen to our team discuss how rf IDEAS is merging the physical access and logical access markets together by enabling access beyond the door.

What is Passkey Authentication?
What is passkey authentication? Learn how passkeys redefine security measures and streamline user authentication across systems and devices.

Why Logical Access Control Is Your Most Essential Defense Against Cyberthreats
Why is access control important? Learn how logical access control mitigates cybersecurity risks and enhances security across the organization.

What Is a Logical Access Control Audit? 3 Steps for Success
Learn what should be included in your organization’s logical access control audit checklist to keep your sensitive assets secure.

3 Reasons to Replace Magnetic Stripe Card Readers Across Your Campus
Learn how migrating from magnetic stripe card readers to contactless technology can increase security and improve the student experience.

The Ultimate Guide to HMI Security: What Manufacturers Need to Know
Learn how you can increase HMI security and enhance workforce productivity with authentication solutions from rf IDEAS.

Why Passwordless Authentication Is Your Best Defense Against Cyber Threats
Learn more about passwordless authentication solutions and why password-centric security is a thing of the past.

The Best Smart Card Readers of 2024
Learn more about passwordless authentication solutions and why password-centric security is a thing of the past.

The Best Mobile Credential Readers of 2024
Learn more about passwordless authentication solutions and why password-centric security is a thing of the past.

Kofax Software Card Readers: Seamlessly Migrating to rf IDEAS
Kofax, a leader in document automation and security software, has recently announced that they will be discontinuing their line of card readers. In response, we at rf IDEAS have created a seamless process to migrate your existing Kofax card readers to rf IDEAS card readers.

Arming manufacturers with a passwordless solution to access and accountability
Manufacturing is one of the most attacked industries by cyber criminals, but a passwordless authentication strategy can help protect your business.

Passkeys: What They Are and How You Can Use Them for Safe, Passwordless Authentication
Discover how you can implement passkeys with rf IDEAS Converge ID technology and effectively eliminate cyber attacks today.

Enhancing Healthcare Cybersecurity Managing Identity Access
Tap-and-go functionality pairs with our WAVE ID readers to protect data, streamline workflows, and offer seamless integration into existing systems.

Smart cards vs. proximity cards — what's the difference?
Discover the differences between proximity and smart cards and why more and more companies are adopting smart cards for secure access with rf IDEAS WAVE ID technology.

FIDO2 standard promises to eliminate the risk of passwords
FIDO2 authentication with rf IDEAS Converge ID technology elevates your security and integrates easily into existing protocols.

The simple steps to migrate to mobile authentication
In today’s highly mobilized environment, many organizations are migrating to a mobile authentication strategy. Whether you are using physical credentials, ID badges, or you don’t have any credentials at all, follow this guide to discover how easy it is to get started building your own mobile strategy.

Healthcare Cybersecurity and the 2023 Omnibus Bill
Discover how the new 2023 Omnibus Bill will affect healthcare HIPAA cybersecurity and learn how to streamline authentication with our WAVE ID Embedded OEM readers. Embedding security within each device

How and why to migrate to mobile credentials
Many organizations are migrating from conventional ID badges to the convenient security of mobile credentials. Learn how easy the transition can be.

What is the future of digital wallet security?
The future of access via phone is here – and the possibilities this offers for employee badges is growing. Learn how with the tap of your phone you can now authenticate access to workstations, printers and other secure enterprise systems. The future of authentication is in the digital wallet.

NFC vs BLE credentials: Determine which is right for you
Mobile authentication using smartphones is secure and easy to manage. But should you choose BLE or NFC? Understand the pros and cons, so you can choose the right technology for your organization’s needs. Read our blog.

It's 99.9% more secure? Answering your MFA FAQs
If you’ve been wondering whether multi-factor authentication is right for your organization, the answer is probably yes. Learn why, and which MFA solutions could be the best choice for your particular security and productivity requirements. Read the blog.

How to implement secure authentication in healthcare
Cyber criminals have become highly sophisticated, and healthcare organizations are a high-value target. How can you protect health information and document compliance with regulations such as HIPAA while giving your staff more time to provide better care?

RFID Card Solutions: Here Today, Here Tomorrow
According to The Business Research Company, the global RFID card market is expected to grow from $9.43 billion in 2021 to $10.31 billion in 2022. Yet as innovative solutions emerge for secure authentication, why do the ubiquitous keycard and RFID card reader continue to play such a vital role in logical access control? Here are a few reasons.

The Cheap Smart Card Reader That Almost Cost Millions
If you’ve ever thought about cutting corners when purchasing identity access management (IAM) hardware, consider what happened in spring 2022 to the U.S. Department of Defense (DoD).

Why to use the multi-factor authentication approach
Beyond the government cybersecurity executive order, every commercial enterprise needs to take action for a secure, productive future. Even businesses not directly affected by government-imposed cybersecurity orders are still at risk of cyberattacks. In fact, the danger is considerably higher today than it was just a year ago. As more government-related enterprises reinforce the systems that protect access to their digital infrastructure and data, hackers are turning their attention to commercial enterprises that have failed to recognize and repair the chinks in their armor.

Four ways to improve cybersecurity for manufacturing
Just as banking, insurance, and government leaders were forced to quickly ramp up cyber defenses in the past few years, manufacturing professionals must today make securing their technologies, production lines, facilities, and processes a top priority. As companies expand their connectivity and reliance on cloud computing, major security gaps emerge. And that means the potential for big problems.

Secure Logical Access for the Commercial Enterprise: Simple Solutions for an Urgent Need
More than 1,000 data breaches have been reported in a single year In the United States at an average cost of $3.92 million each in losses and fines.1 Up to 88% of UK companies suffered data breaches in a single year at an average cost of £2.85 million. Successful hacks of small businesses in the UK occurred every 19 seconds.2

2021 Was the Year of New Technologies
Let’s get it out of the way: it’s impossible to talk about 2021 without talking about how companies responded to the pandemic. It has presented challenges and upended numerous business models, and the RFID industry isn’t any different. But 2021 also saw some amazing technological developments, especially when it comes to our WAVE ID® technology, innovations in applications and form factors, and the continuing explosion of mobile, MFA and BLE technology.

Responding to the New MFA Mandate
On May 12, 2021, President Joe Biden signed an executive order mandating the Federal Government to partner with the private sector in a multipronged campaign to protect the government agencies, private enterprises and American people against the threat of increasingly sophisticated cyberattacks.
Anyone who follows the news can understand why—and especially why now.

Touchless Technology for a Healthy Workplace
The coronavirus crisis demands a rapid response to protect essential workers. RimotHEALTH’s new contactless entry-screening and attendance-tracking kiosk, featuring rf IDEAS® technology, will be improving workplace safety long after the current crisis has passed.

Contact Tracing Software Puts Partnership on the Fast Track
Contactless attendance tracking software and authentication solutions are already playing a critical role in office environments, schools (related article here) and healthcare facilities. Recently, a major healthcare provider engaged rf IDEAS® and partner World Wide Technology (WWT) to implement a contact tracing solution across 800 locations serving thousands of employees… all in four weeks.

Information Is One Thing, Action Is Another
Our friends and partners at Imprivata recently completed a survey of healthcare executives, association members and CIOs to better understand how COVID-19 has directly affected their individual organizations’ Identity Management solutions. After reading through the results and analysis from the Imprivata team (related article found here), I would like to share what we at rf IDEAS have been doing to support Imprivata’s new efforts.

Technology Trends 2021: 5 Hot Topics to Look for in the RFID Industry
While 2020 will be remembered as the year we all worked from home, 2021 promises a return to productivity with workplaces reopening and authentication technologies shifting to meet new demands.

FIDO2 and WAVE ID® Readers: Fewer Passwords, Greater Security
Take a quick peek at your to-do list. Chances are, changing or strengthening your password(s) is not at the top of the list. And while it’s understandable that we all have other priorities, the downside of weak or stolen passwords is the potential for damaging and costly data breaches.

Touch-Free Secure Print for Businesses Returning to the Workplace
The current pandemic has forced virtually every organization on the planet to transform their approaches to workplace productivity. As a vaccine starts to become a reality, many of the world’s leading companies are already focused on back-to-office strategies and long-term planning for safer on-site operations.

The advantages and misconceptions of biometric authentication
With the upcoming release of our WAVE ID® Bio reader, rf IDEAS now offers an all-in-one solution for multi-factor authentication that’s both super secure and super easy. It provides a biometric fingerprint reader, a Bluetooth® Low Energy mobile credential reader and a proximity/smart card reader in one sleek, modern, plug-and-play device that only consumes one USB port.

Simplifying School Contact Tracing with Help from i-Attend and rf IDEAS
Event and attendance tracking plays an important role across educational settings. Students use identity cards and mobile credentials for classroom attendance, equipment check-out, accessing the library or school bus, meal plans and secure entry and access across campus facilities.

Three New RFID Reseller Insights for a Different World.
Time flies. It’s been two and a half years since I shared Three Insights for a Successful RFID Reseller with rf IDEAS for publication on their blog. Readership has been strong, and the relationship between rf IDEAS and Windmill Computing has continued to grow over the years, for which I’m grateful. But I’m often asked, “What has changed since then?”

The Future of Identity Access Management (IAM) in Healthcare
In this interview, Wright explains how Imprivata and rf IDEAS collaborate on new authentication technologies to bring unsurpassed efficiency and security to busy healthcare environments.

Choose Mobile Access for Simple, Safe and Secure Multi-Factor Authentication
As the logical access control pioneer and long-time leader, rf IDEAS is laser-focused on the opportunities for mobile access. Our WAVE ID® Mobile Readers work with today’s most widely used mobile credentials—including HID® Mobile Access, Orange Business Services Pack ID and Safetrust Wallet—while simultaneously supporting virtually every proximity and smartcard technology used worldwide.

Working From Home Is Suddenly in Style. Working Safely Always Has Been. Here’s How to Do It.
Username and password schemes bring multiple risks, from weak and stolen passwords to shared keyboards that can spread pathogens. rf IDEAS has simple suggestions for avoiding these threats while enabling users to be more productive—at home and in the office.

EPCS and 2FA: Authentication on the Frontlines of the Opioid Crisis
As we all know, the long, national nightmare known as the opioid crisis continues to drag on across the U.S. According to a recent American Psychiatric Association poll, nearly one of three Americans knows someone addicted to some form of opioid. And, according to the CDC, on average, 130 Americans die every day from an opioid overdose.

IAM is now a Top 10 Strategic Priority for State Governments
When it comes to IAM, state governments are concerned about managing access for both their employees and the citizens they serve. According to Doug Robinson, NASCIO’s executive director, “enterprise IAM approaches and solutions are gaining more traction in the states and are essential for managing secure employee access and supporting digital government platforms for citizens.”

No Single Badge to Rule Them All
User badge authentication should simplify lives and wallets – not add an additional layer of complexity.

How to securely improve access control in healthcare
With more than 60% of the world’s population owning a mobile phone, business use of smartphones has become ubiquitous for the workforce around the world.

THE ROI OF SSO: How Single Sign-On Is Paying Off for Hospitals
With login processes continuing to be a complex and costly issue, more and more hospitals are implementing single sign-on (SSO) technology for the promise of productivity gains and financial rewards. In fact, today, SSO—the technology that enables users to log on to all the software systems throughout the hospital with a single ID—are now mission-critical for healthcare.

Healthcare for Hospital Keyboards — What’s Lurking in the Crevices of Your Hospital’s Keyboards?
Healthcare workers’ hands often come into contact with blood, secretions, and many other substances in the course of a workday. These substances can be easily spread to the computer keyboard as clinicians input information, review doctor’s orders and navigate application screens. Moreover, keyboards are notoriously hard to clean because bacteria can become lodged beneath and between keys, and in areas that are hard to reach and disinfect.

Drowning in Passwords? You're Not Alone. 5 Reasons Your Business Should Sign on to SSO
When passwords first came into vogue in the early 1960s as a way to secure computers, we couldn’t envision the many ways they’re being used today.

Identity Access Management and the State of CISOs: Where We Are Now
State governments are the guardians of valuable, sensitive data about their citizens, their employees and their operations. From tax and voter information to employee credentials and department files, all of that data is potentially at risk on many fronts.

The New IAM: 5 Challenges That Add New Risks
Identity access and management (IAM), the IT security discipline dedicated to ensuring that the “right persons have access to the right resources at the right time for the right reasons,” has been around since the early 2000s. At that time, organizations and their IT teams were responding organically to the need for managing identity.

Cybercriminals are Targeting your Printers
There could be a security risk hiding in plain sight in your workplace. Consider this: Those hard-working printers scattered throughout your offices could actually be serving as easy entry points for security breaches.

Celebrating National Cyber Security Awareness Month with a Focus on Education
October is National Cyber Security Awareness Month (NCSAM) in the U.S., and during the second week of the month, the focus is on higher education. Data breaches affect organizations across every vertical, yet many of these breaches could be avoided

The Financial Sector’s Gateway to Security & Advanced Functionality
At Kyocera, we strive to offer a total document solution. In today’s world, it’s important to consider a wide variety of factors when designing solutions, including security, accessibility and integration with existing business platforms. Customers come to us with a need to print and scan, and we respond with a complete package that addresses all their business document needs – even ones they may not have considered.

Stay secure with healthcare identity and access management
Printing is a hidden cost that many organizations find hard to quantify. Beyond the price of physical materials such as equipment, paper and toner, there also are costs associated with maintenance, departments “doing their own thing” and even the opportunity cost of time spent waiting at the printer for a job to print.

The Summer Tasks of an Educational Network Administrator
Without authentication, there is no security. See how these common security protocols and simplification efforts are relevant to EVERY industry.
rf IDEAS Announces New Embedded and Mobile Credential Readers for Healthcare at HIMSS 2018
rf IDEAS, Inc., a leading innovator and manufacturer of employee RF credential readers for in-building applications such as computer access, identification, secure pull print, time and attendance, will showcase its new OEM and Embedded Readers and its Mobile Credential Readers with Bluetooth® low energy technology.
Recognizing the Benefits of Smart Authentication in Manufacturing
In the manufacturing world, it’s often hard to tangibly account for the benefits of RFID-enabled authentication. RFID operator authentication technology helps from the moment we enter the workplace to the moment we sign out, and everywhere in between. The benefits, although not often top-of-mind, expand beyond simplifying our daily tasks, into helping us be in compliance with industry regulations.

Consultative Selling Shows Insight into Printing's Demands
At ACDI, we're specialists in unbiased, consultative selling. Launched in 1994 as a hardware provider, we originally specialized in coin-op machines, among other hardware, for convenience printing. Sensing the shift in market demands, we made a switch to include software solutions in our product portfolio in 2011. Seven years later, software has become our largest revenue driver, and we're currently positioned as the largest PaperCut™ Authorized Solution Center (ASC) across the globe.

How Technology Can Answer Some of the Healthcare Environment's Pressing Needs
Like any industry, healthcare has a unique set of considerations, specifically when it comes to protecting its people – both patients and employees.

Three Insights for a Successful RFID Reseller
In the 10+ years since Windmill Computing became a distributor for RF IDeas, we've formed a long-standing relationship with the RFID community. We've learned a few tips on what it takes to be a successful reseller.

GDPR Affects Us All. Here's How.
On May 25, 2018, the General Data Protection Regulation (GDPR) will go into effect. Residing in the U.K., I hear a lot about the upcoming deadline, and the implications it has on European Union (EU) citizens.

Mobilizing RFID in Mustering for Critical Attendance Management Tasks
Mustering is a critical part of any disaster plan and involves accounting for personnel during an emergency. With the rise of RFID-based access control, many companies manage this process through the facility's access control system. In order for this process to be efficient and accurate, the data must be accessible from a mobile device. Sitting at a centralized workstation inside a building that is on fire will not work. During an evacuation, attendance is taken outside at muster points, far away from the building’s doorway and wired readers.

How to Successfully Deploy a Secure Print Solution
To help deploy a successful secure print solution, regardless of where you are in the adaptation process, we've come up with a list of helpful tips

Three Printer Risks and How to Avoid Them
Most people don't think about printing when they consider security breaches on the job. In fact, HP recently found that 56 percent of companies ignore printers in their endpoint security strategy. But with security breaches happening all over the office, both relating to physical and logical security, thinking of printer risks is a must-do for a complete security strategy.

Holistic Security with Authentication Across the Manufacturing Floor
Diving deeper into the first element, security assessment, can be a daunting task. What elements of my building should be considered? Did I forget a point of vulnerability? How can I possibly ensure ever element of my building is secure?
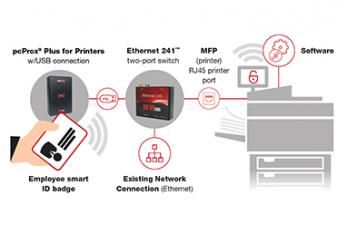
Think Authentication Solutions for MFP are a Waste? Think Again.
Implementing an extra layer of security in the office can send some heads spinning. Is this going to take me extra time? Will I have to remember a password?

Avoiding OSHA Violations with Simple RFID Implementation
Manufacturing is a behind-the-scenes operation that, while vital to all organizations, often gets little attention. When operations are running smoothly, everyone from the shareholders to the customers remain happy

Expanding Security; Exploring the Logical Transition
The word security takes on many different definitions depending on the lens in which it is perceived. To an infant, security is the caring arms of a mother or father. A homeowner sees it as protection of their property. There's financial security and security in one's self. Perhaps the multitude of definitions can help explain why a simple Google search of the word security results in more than 1.8 billion results.
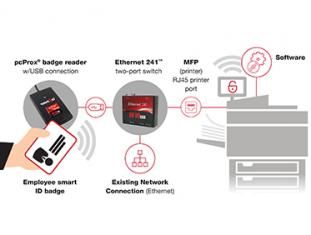
Secure Printing Just Got Easier With Ethernet 241 and Discovery Tool
Security doesn’t just end at the door. It extends throughout the entire enterprise, including the organization’s print devices, whether multi- or single-function.

University Uses RF IDeas Readers to Reduce Access Cards from Several to One
Founded in 1925, a private educational institution on the North America east coast offers low-cost, part-time evening studies in law and business for working adults. The school has expanded to include a College of Public Affairs and College of Arts and Sciences. The majority of its 6,500 students and 900 faculty and staff commute to campus on a daily basis.

Main Line Health System
Improving infection control and ensuring patient confidentiality. A not-for-profit health system serving portions of Philadelphia and its western suburbs, Main Line Health offers acute and non-acute care through seven health care facilities, a multi-specialty physician network, and the Lankenau Institute for Medical Research.
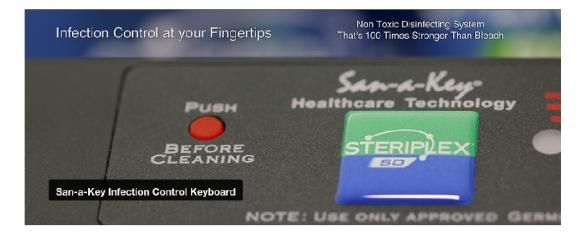
Improving Security and Infection Control in One Keyboard
From the recent Ebola scare to the current measles epidemic, the emphasis on disease control and preventing the spread of infection has never been more critical. But sometimes it’s the littlest things that can make the biggest difference.

Going Beyond the Door
Most mid- to large-size organizations today in nearly all industries leverage employee ID badges to authorize automated access to the premises. However, physical access to a building is just one way employee badges can be used to address challenges faced by these organizations.